Prevention is the Ultimate Defense
Powered by AI & Humans 24/7
All-in-One Cybersecurity
Prevention is the Ultimate Defense Powered by AI & Humans 24/7

We Manage Next-Gen SIEM
We monitor all your systems in real time and analyze logs from, critical systems, hardware, etc.
Vulnerability Management
We continuously scan and assess your internal & external infrastructure, devices, and cloud systems
Experienced support team
Our dedicated SOC team proactively monitors your systems 24/7 and responds immediately
Next-Gen penetration testing
Protect your business by exposing weaknesses and reinforcing defenses with Next-Gen Pentest
awareness training
Modern security awareness, combining engaging training, phishing simulations, and AI-driven tools
phishing simulation
Fully customizable phishing tests with uploads, login traps, detailed tracking per user & company
GAP Overview
Structured GAP view with tasks, roles, deadlines, live progress, notifications, notes & documentation
ISCP
Create your full IT contingency plan with easy templates, responsibilities, documentation & etc.
Risk Management
Identify, assess, and document risks with easy templates, impact levels, and mitigation actions








Top Integration Partners








Protect Your Business with Cyber Detector
Protect Your Business with Cyber Detector
We help your business safeguard itself against cyberattacks, so you can focus on what’s important to you.
We help your business safeguard itself against cyberattacks, so you can focus on what’s important to you.

All-in-One Cybersecurity
Next-Gen SEIM
Our most popular feature. Integrate seamlessly with your systems and gain centralized visibility of all security events in your workspace.
Vulnerability Management
Our Vulnerability Management solution is the perfect tool trusted by our customers to proactively identify and address security risks, ensuring comprehensive protection.
Experienced support team
Awareness Training
Empower Your Team to Stay Cyber-Safe
CyberLearn helps employees build strong security habits through engaging awareness training, AI-driven microlearning, and real-life scenarios tailored to your organization.
Phishing Simulation
Test, Train & Track Real-World Cyber Behavior
CyberLearn’s phishing simulation module lets you send realistic phishing emails, simulate login traps, and track user responses – so you can measure awareness and strengthen defenses. Read more about CyberLearn
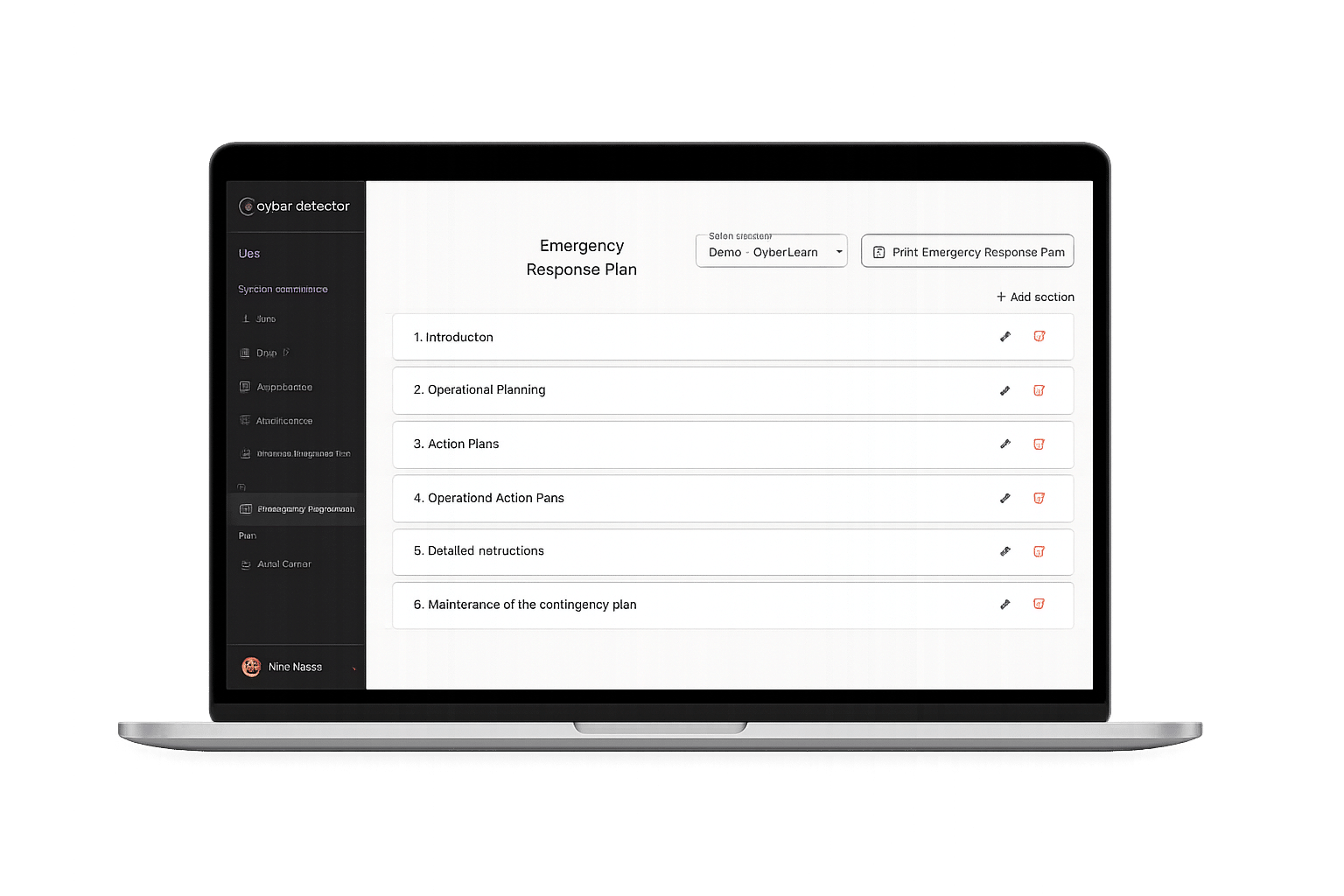

ISCP
ISCP (Information System Contingency Plan) helps your organization prepare for cyber incidents with structured templates, responsibilities, and documentation. It ensures that you can respond effectively and maintain business continuity.
GAP Overview
The GAP Overview gives you a clear structure to manage compliance tasks. Assign roles, set deadlines, track progress, and document actions across areas and certificates – all in one visual dashboard.
Risk Management
Risk Management in CyberLearn allows you to identify, assess, and document risks using standardized templates. Evaluate likelihood and impact, define mitigation actions, and maintain full traceability for audits and reviews.
What We Offer
What We Offer

Real-time Monitoring
We provide constant monitoring of both new and existing risks, keeping your security always up-to-date. See overview
Comprehensive Analysis & reports
Our library of analyses keeps you informed of changes in the threat landscape as they occur.
Adaptive Security
Our systems automatically detect and scan new devices as soon as they connect to your network and quickly identify devices with critical vulnerabilities.
E-learning
Cyber eLearning equips employees with the knowledge to strengthen your first line of defense, ensuring hackers can't breach your organization through human error.
Three Easy Steps
01
Step 01
Reach out to us to discuss your IT needs. Begin optimizing your IT infrastructure with a free, no-obligation consultation. In this initial session, we’ll take the time to understand your business and its unique challenges, ensuring we align our solutions with your specific IT requirements and objectives.
02
Step 02
Create a tailored IT strategy with us. Through close collaboration, we develop a personalized IT plan that aligns seamlessly with your company’s needs and goals, considering both your existing systems and future technology trends to ensure long-term success.
03
Step 03
Efficient implementation and seamless integration. We ensure a swift and smooth implementation, seamlessly integrating our solutions into your existing business processes. Our approach minimizes disruptions, maximizes IT system efficiency, and allows you to stay focused on what matters most—your core business.
Why Choose Us
Everything You Need In One System
Everything You Need In One System
All In One Place
Cyber Detector – More Than Cybersecurity
We deliver holistic IT security solutions tailored to your needs, covering monitoring, analysis, support, and threat prevention in one platform.
Cyber Protector – Advanced, AI-driven detection and response to evolving threats.
Cyber eLearning – Empower employees with engaging Security Awareness Training to prevent attacks.
Cyber DarkWeb – Stay ahead of dark web threats with live searches and domain alerts.
Penetration Test – Detect vulnerabilities before attackers do.
Our AI Detector ensures full visibility, streamlined administration, and smarter threat management, so you can focus on your business while we secure it.
SIEM (Security Information and Event Management)
Our foundation at Cyber Detector is based on SIEM (Security Information and Event Management). SIEM is an advanced system that collects and analyzes security data across the entire organization. It enables real-time monitoring, helping to detect potential threats and manage security incidents quickly and effectively.
Additionally, SIEM ensures compliance with regulatory requirements and provides a clear overview of the organization’s security situation, ultimately reducing the time spent on administration.
Daily Infrastructure Analysis
We offer a proactive review of your network and systems to identify and mitigate potential security risks. Our vulnerability management includes a comprehensive analysis and evaluation of possible security vulnerabilities in your infrastructure. This process allows our support team to detect potential attack vectors before a threat is activated. Using a risk score scale from 1 to 1,000, we highlight the vulnerabilities most likely to be exploited. This helps you focus on and prioritize the most critical security issues.
Why Choose Us
Everything You Need In One System
Everything You Need In One System
All In One Place
Cyber Detector offers more than cybersecurity — we deliver tailored IT security solutions, including monitoring, analysis, support, and threat prevention.
Our products:
- Cyber Inspector
- CyberLearn
- Cyber PenTEST
With our products, gain full security visibility, reduce admin time, and focus on growing your business.
Intuitive and user-friendly
Cyber Detector's platforms are designed to be intuitive and user-friendly, ensuring that our users can navigate and operate with ease. We prioritize simplicity without compromising on advanced functionality, allowing businesses to manage their cybersecurity effectively without needing extensive technical expertise. With streamlined interfaces and clear workflows, Cyber Detector delivers powerful security solutions that anyone can utilize confidently.
Our vision
We want to provide small and medium-sized businesses with access to advanced IT security systems All-in-One Cybersecurity typically available only to large enterprises . Our goal is to offer solutions at a price point that everyone can afford without compromising on quality. At Cyber Detector, we believe that all businesses, regardless of size, deserve effective protection against cyber threats—delivered in a simple, reliable, and cost-effective way.

